 VietNam Hack CCV Tools
VietNam Hack CCV Tools
Friday, November 27, 2009 | Posted By
Edy Wardoyo |
Edit Post

VietNam Hacks CCV Tools
this feature
1.search shop with google automatics
2.google url extraxtor
3.check sql programs
4.sql injection tools
5.join query attack
And many others...........
U CAN DOWNLOAD HERE
source: google.com
 Software to Block_usb
Software to Block_usb
Sunday, November 22, 2009 | Posted By
Edy Wardoyo |
Edit Post
Block USB

This tool is used to block the usb into the computer, so when you plug the usb into the pc the usb can not detect the cpu
This software compiled using C programs, only 55 kb size
Download Here

This tool is used to block the usb into the computer, so when you plug the usb into the pc the usb can not detect the cpu
This software compiled using C programs, only 55 kb size
Download Here
 google tools
google tools
Saturday, November 21, 2009 | Posted By
Edy Wardoyo |
Edit Post
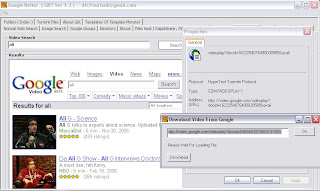
google tools
Feature this tools :
1.Looking for application made easy
2.file in host (ex. in rapidshare)
3.looking for pdf file
4.looking for torrent file
and many feature of this tools
U CAN DOWNLOAD HERE:
 45 Hacking Tools
45 Hacking Tools
Sunday, November 15, 2009 | Posted By
Edy Wardoyo |
Edit Post

Features:
• IMC Grahams Trojan
• IMC Ice Dragon
• Myspace Password Cracker
• IMC Myspace Phisher
• Ultra Surf
• Rapid Share *** Gen
• MSN Nudge Madness
• Ice Reloaded MSN Freezer
• IMC Handbook
• BrutusAE2
• Lord PS
• Hoax Toolbox
• IMC Word List
• Blues Port Scanner
• Bandook RAT v1.35
• Project Satan 2.0
• EES binder v1.0
• File Injector v3
• Remote Desktop Spy v4.0
• Passive Terror v1.3 Final Edition
• Dyn-DL (Dynamic downloader)
• Silent Assassin v2.0
• Net Scan Tools v4.2
• Rocket v1.0
• NStealth HTTP Security Scanner v5.8
• Attack Toolkit v4.1 & source code included
• Legion NetBios Scanner v2.1
• Battle Pong
• TeraBIT Virus Maker v2.8
• p0kes WormGen 2.0
• JPS Virus Maker
• IRC Ban Protection
• IRC Mega Flooder
• FTP Brute Hacker
• RAR Password Cracker
• Vbulletin 3.6.5 Sql Injection Exploit
• IPB 2-2.1.5 Sql Injection Exploit
• IPB 2-2.1.7 Exploit
• Cain & Abel v4.9.3
• NetStumbler 0.4.0
• Cryptor 1.2
• VNC Crack
• Hamachi 0.9.9.9
• pbnj-1.0
• Mutilate File Wiper 2.92
• and many more...
DOWNLOAD HERE
I take this software from google
 Swiss Army Knife V4 (free ware)
Swiss Army Knife V4 (free ware)
Wednesday, November 11, 2009 | Posted By
Edy Wardoyo |
Edit Post
Swiss Army Knife V4 (free ware)
feature :
An offline phisher
A binder (this maybe FUD but more then likely its just UD)
Screen shot tool
Batch File Generator
On Screen Keyboard
There is also a "lite" version of the program included that doesnt have the web browser
Fully functional Web Browser (except saving things to favorites)
A CC (credit card) validator
Byte Adder
A super email tool
A port checker
A User Creator
note : the Last Activity shows the last time your mouse or keyboard was touched..so if you
enable that and leave your computer and the time changes..u'll know some1 bothered your
stuff :)
u can download HERE
source from google write by VendettaSoldier www.hackforums.net
feature :
An offline phisher
A binder (this maybe FUD but more then likely its just UD)
Screen shot tool
Batch File Generator
On Screen Keyboard
There is also a "lite" version of the program included that doesnt have the web browser
Fully functional Web Browser (except saving things to favorites)
A CC (credit card) validator
Byte Adder
A super email tool
A port checker
A User Creator
note : the Last Activity shows the last time your mouse or keyboard was touched..so if you
enable that and leave your computer and the time changes..u'll know some1 bothered your
stuff :)
u can download HERE
source from google write by VendettaSoldier www.hackforums.net
 How To Boot Xp Very Faster
How To Boot Xp Very Faster
Tuesday, November 10, 2009 | Posted By
Edy Wardoyo |
Edit Post
First of all, this tweak only apply to those who only have one HDD on their primary IDE channel (nothing else on device 0 or 1) and a CD-ROM and/or DVD-ROM on the secondary IDE channel. Each time you boot Windows XP, there's an updated file called NTOSBOOT-*.pf who appears in your prefetch directory (%SystemRoot%Prefetch) and there's no need to erease any other files as the new prefetch option in XP really improves loading time of installed programs. We only want WindowsXP to boot faster and not decrease its performance. Thanks to Rod Cahoon (for the prefetch automation process...with a minor change of mine) and Zeb for the IDE Channel tweak as those two tricks, coupled together with a little modification, result in an EXTREMELY fast bootup:
1. Open notepad.exe, type "del c:windowsprefetch tosboot-*.* /q" (without the quotes) & save as "ntosboot.bat" in c:
2. From the Start menu, select "Run..." & type "gpedit.msc".
3. Double click "Windows Settings" under "Computer Configuration" and double click again on "Shutdown" in the right window.
4. In the new window, click "add", "Browse", locate your "ntosboot.bat" file & click "Open".
5. Click "OK", "Apply" & "OK" once again to exit.
6. From the Start menu, select "Run..." & type "devmgmt.msc".
7. Double click on "IDE ATA/ATAPI controllers"
8. Right click on "Primary IDE Channel" and select "Properties".
9. Select the "Advanced Settings" tab then on the device 0 or 1 that doesn't have 'device type' greyed out select 'none' instead of 'autodetect' & click "OK".
10. Right click on "Secondary IDE channel", select "Properties" and repeat step 9.
11. Reboot your computer.
WindowsXP should now boot REALLY faster.
source : www.Google.com
1. Open notepad.exe, type "del c:windowsprefetch tosboot-*.* /q" (without the quotes) & save as "ntosboot.bat" in c:
2. From the Start menu, select "Run..." & type "gpedit.msc".
3. Double click "Windows Settings" under "Computer Configuration" and double click again on "Shutdown" in the right window.
4. In the new window, click "add", "Browse", locate your "ntosboot.bat" file & click "Open".
5. Click "OK", "Apply" & "OK" once again to exit.
6. From the Start menu, select "Run..." & type "devmgmt.msc".
7. Double click on "IDE ATA/ATAPI controllers"
8. Right click on "Primary IDE Channel" and select "Properties".
9. Select the "Advanced Settings" tab then on the device 0 or 1 that doesn't have 'device type' greyed out select 'none' instead of 'autodetect' & click "OK".
10. Right click on "Secondary IDE channel", select "Properties" and repeat step 9.
11. Reboot your computer.
WindowsXP should now boot REALLY faster.
source : www.Google.com
 make your browser snowy
make your browser snowy
Monday, November 09, 2009 | Posted By
Edy Wardoyo |
Edit Post
in this case we use java script program, some browser maybe block this script, so u just allow the run active content
to get code please download here
after you download this scrip
u can download the picture here
having fun....
to get code please download here
after you download this scrip
u can download the picture here
having fun....
 Executing CMD Programs Using a URL in IE
Executing CMD Programs Using a URL in IE
Monday, November 09, 2009 | Posted By
Edy Wardoyo |
Edit Post
when u have problem with dos program,ex admin block access dos program in windows maybe make u bored, but don't worry i have the way out to solve your problems
step 1.
1. Right-click on the Desktop
step 2
2. Create a new Shortcut
step 3
3. Point the location of the item to any executable... such as: c:\windows\system32\cmd.exe
step 4
4. Name the shortcut, for example, www.Google.com
step 5
5. Start Internet Explorer
step 6
6.Type www.Google.com" into the address bar
nice try.....
source : WWW.Google.com
step 1.
1. Right-click on the Desktop
step 2
2. Create a new Shortcut
step 3
3. Point the location of the item to any executable... such as: c:\windows\system32\cmd.exe
step 4
4. Name the shortcut, for example, www.Google.com
step 5
5. Start Internet Explorer
step 6
6.Type www.Google.com" into the address bar
nice try.....
source : WWW.Google.com
 Cracking Zip Password Files
Cracking Zip Password Files
Monday, November 09, 2009 | Posted By
Edy Wardoyo |
Edit Post
Tut On Cracking Zip Password Files..
What is FZC? FZC is a program that cracks zip files (zip is a method of compressing multiple files into one smaller file) that are password-protected (which means you're gonna need a password to open the zip file and extract files out of it). You can get it anywhere - just use a search engine such as altavista.com.
FZC uses multiple methods of cracking - bruteforce (guessing passwords systematically until the program gets it) or wordlist attacks (otherwise known as dictionary attacks. Instead of just guessing passwords systematically, the program takes passwords out of a "wordlist", which is a text file that contains possible passwords. You can get lots of wordlists at www.theargon.com.).
FZC can be used in order to achieve two different goals: you can either use it to recover a lost zip password which you used to remember but somehow forgot, or to crack zip passwords which you're not supposed to have. So like every tool, this one can be used for good and for evil.
The first thing I want to say is that reading this tutorial... is the easy way to learn how to use this program, but after reading this part of how to use the FZC you should go and check the texts that come with that program and read them all. You are also going to see the phrase "check name.txt" often in this text. These files should be in FZC's directory. They contain more information about FZC.
FZC is a good password recovery tool, because it's very fast and also support resuming so you don't have to keep the computer turned on until you get the password, like it used to be some years ago with older cracking programs. You would probably always get the password unless the password is longer than 32 chars (a char is a character, which can be anything - a number, a lowercase or undercase letter or a symbol such as ! or &) because 32 chars is the maximum value that FZC will accept, but it doesn't really matter, because in order to bruteforce a password with 32 chars you'll need to be at least immortal..heehhe.. to see the time that FZC takes with bruteforce just open the Bforce.txt file, which contains such information.
FZC supports brute-force attacks, as well as wordlist attacks. While brute-force attacks don't require you to have anything, wordlist attacks require you to have wordlists, which you can get from www.theargon.com. There are wordlists in various languages, various topics or just miscellaneous wordlists. The bigger the wordlist is, the more chances you have to crack the password.
Now that you have a good wordlist, just get FZC working on the locked zip file, grab a drink, lie down and wait... and wait... and wait...and have good thoughts like "In wordlist mode I'm gonna get the password in minutes" or something like this... you start doing all this and remember "Hey this guy started with all this bullshit and didn't say how I can start a wordlist attack!..." So please wait just a little more, read this tutorial 'till the end and you can do all this "bullshit".
We need to keep in mind that are some people might choose some really weird passwords (for example: 'e8t7@$^%*gfh), which are harder to crack and are certainly impossible to crack (unless you have some weird wordlist). If you have a bad luck and you got such a file, having a 200MB list won't help you anymore. Instead, you'll have to use a different type of attack. If you are a person that gives up at the first sign of failure, stop being like that or you won't get anywhere. What you need to do in such a situation is to put aside your sweet xxx MB's list and start using the Brute Force attack.
If you have some sort of a really fast and new computer and you're afraid that you won't be able to use your computer's power to the fullest because the zip cracker doesn't support this kind of technology, it's your lucky day! FZC has multiple settings for all sorts of hardware, and will automatically select the best method.
Now that we've gone through all the theoretical stuff, let's get to the actual commands.
--------------------------------------------------------------------------------
Bruteforce
--------------------------------------------------------------------------------
The command line you'll need to use for using brute force is:
fzc -mb -nzFile.zip -lChr Lenght -cType of chars
Now if you read the bforce.txt that comes with fzc you'll find the description of how works Chr Lenght and the Type of chars, but hey, I'm gonna explain this too. Why not, right?... (but remember look at the bforce.txt too)
For Chr Lenght you can use 4 kind of switches...
-> You can use range -> 4-6 :it would brute force from 4 Chr passwors to 6 chr passwords
-> You can use just one lenght -> 5 :it would just brute force using passwords with 5 chars
-> You can use also the all number -> 0 :it would start brute forcing from passwords with lenght 0 to lenght 32, even if you are crazy i don't think that you would do this.... if you are thinking in doing this get a live...
-> You can use the + sign with a number -> 3+ :in this case it would brute force from passwords with lenght 3 to passwords with 32 chars of lenght, almost like the last option...
For the Type of chars we have 5 switches they are:
-> a for using lowercase letters
-> A for using uppercase letters
-> ! for using simbols (check the Bforce.txt if you want to see what simbols)
-> s for using space
-> 1 for using numbers
Example:
If you want to find a password with lowercase and numbers by brute force you would just do something like:
fzc -mb -nzTest.zip -l4-7 -ca1
This would try all combinations from passwords with 4 chars of lenght till 7 chars, but just using numbers and lowercase.
*****
hint
*****
You should never start the first brute force attack to a file using all the chars switches, first just try lowercase, then uppercase, then uppercase with number then lowercase with numbers, just do like this because you can get lucky and find the password much faster, if this doesn't work just prepare your brain and start with a brute force that would take a lot of time. With a combination like lowercase, uppercase, special chars and numbers.
--------------------------------------------------------------------------------
Wordlis
--------------------------------------------------------------------------------
Like I said in the bottom and like you should be thinking now, the wordlist is the most powerfull mode in this program. Using this mode, you can choose between 3 modes, where each one do some changes to the text that is in the wordlist, I'm not going to say what each mode does to the words, for knowing that just check the file wlist.txt, the only thing I'm going to tell you is that the best mode to get passwords is mode 3, but it takes longer time too.
To start a wordlist attak you'll do something like.
fzc -mwMode number -nzFile.zip -nwWordlist
Where:
Mode number is 1, 2 or 3 just check wlist.txt to see the changes in each mode.
File.zip is the filename and Wordlist is the name of the wordlist that you want to use. Remember that if the file or the wordlist isn't in the same directory of FZC you'll need to give the all path.
You can add other switches to that line like -fLine where you define in which line will FZC start reading, and the -lChar Length where it will just be read the words in that char length, the switche works like in bruteforce mode.
So if you something like
fzc -mw1 -nztest.zip -nwMywordlist.txt -f50 -l9+
FZC would just start reading at line 50 and would just read with length >= to 9.
Example:
If you want to crack a file called myfile.zip using the "theargonlistserver1.txt" wordlist, selecting mode 3, and you wanted FZC to start reading at line 50 you would do:
fzc -mw3 -nzmyfile.zip -nwtheargonlistserver1.txt -f50
--------------------------------------------------------------------------------
Resuming
--------------------------------------------------------------------------------
Other good feature in FZC is that FZC supports resuming. If you need to shutdown your computer and FZC is running you just need to press the ESC key, and fzc will stop. Now if you are using a brute force attack the current status will be saved in a file called resume.fzc but if you are using a wordlist it will say to you in what line it ended (you can find the line in the file fzc.log too).
To resume the bruteforce attack you just need to do:
fzc -mr
And the bruteforce attack will start from the place where it stopped when you pressed the ESC key.
But if you want to resume a wordlist attack you'll need to start a new wordlist attack, saying where it's gonna start. So if you ended the attack to the file.zip in line 100 using wordlist.txt in mode 3 to resume you'll type
fzc -mw3 -nzfile.zip -nwwordlist.txt -f100
Doing this FZC would start in line 100, since the others 99 lines where already checked in an earlier FZC session.
Well, it looks like I covered most of what you need to know. I certainly hope it helped you... don't forget to read the files that come with the program
What is FZC? FZC is a program that cracks zip files (zip is a method of compressing multiple files into one smaller file) that are password-protected (which means you're gonna need a password to open the zip file and extract files out of it). You can get it anywhere - just use a search engine such as altavista.com.
FZC uses multiple methods of cracking - bruteforce (guessing passwords systematically until the program gets it) or wordlist attacks (otherwise known as dictionary attacks. Instead of just guessing passwords systematically, the program takes passwords out of a "wordlist", which is a text file that contains possible passwords. You can get lots of wordlists at www.theargon.com.).
FZC can be used in order to achieve two different goals: you can either use it to recover a lost zip password which you used to remember but somehow forgot, or to crack zip passwords which you're not supposed to have. So like every tool, this one can be used for good and for evil.
The first thing I want to say is that reading this tutorial... is the easy way to learn how to use this program, but after reading this part of how to use the FZC you should go and check the texts that come with that program and read them all. You are also going to see the phrase "check name.txt" often in this text. These files should be in FZC's directory. They contain more information about FZC.
FZC is a good password recovery tool, because it's very fast and also support resuming so you don't have to keep the computer turned on until you get the password, like it used to be some years ago with older cracking programs. You would probably always get the password unless the password is longer than 32 chars (a char is a character, which can be anything - a number, a lowercase or undercase letter or a symbol such as ! or &) because 32 chars is the maximum value that FZC will accept, but it doesn't really matter, because in order to bruteforce a password with 32 chars you'll need to be at least immortal..heehhe.. to see the time that FZC takes with bruteforce just open the Bforce.txt file, which contains such information.
FZC supports brute-force attacks, as well as wordlist attacks. While brute-force attacks don't require you to have anything, wordlist attacks require you to have wordlists, which you can get from www.theargon.com. There are wordlists in various languages, various topics or just miscellaneous wordlists. The bigger the wordlist is, the more chances you have to crack the password.
Now that you have a good wordlist, just get FZC working on the locked zip file, grab a drink, lie down and wait... and wait... and wait...and have good thoughts like "In wordlist mode I'm gonna get the password in minutes" or something like this... you start doing all this and remember "Hey this guy started with all this bullshit and didn't say how I can start a wordlist attack!..." So please wait just a little more, read this tutorial 'till the end and you can do all this "bullshit".
We need to keep in mind that are some people might choose some really weird passwords (for example: 'e8t7@$^%*gfh), which are harder to crack and are certainly impossible to crack (unless you have some weird wordlist). If you have a bad luck and you got such a file, having a 200MB list won't help you anymore. Instead, you'll have to use a different type of attack. If you are a person that gives up at the first sign of failure, stop being like that or you won't get anywhere. What you need to do in such a situation is to put aside your sweet xxx MB's list and start using the Brute Force attack.
If you have some sort of a really fast and new computer and you're afraid that you won't be able to use your computer's power to the fullest because the zip cracker doesn't support this kind of technology, it's your lucky day! FZC has multiple settings for all sorts of hardware, and will automatically select the best method.
Now that we've gone through all the theoretical stuff, let's get to the actual commands.
--------------------------------------------------------------------------------
Bruteforce
--------------------------------------------------------------------------------
The command line you'll need to use for using brute force is:
fzc -mb -nzFile.zip -lChr Lenght -cType of chars
Now if you read the bforce.txt that comes with fzc you'll find the description of how works Chr Lenght and the Type of chars, but hey, I'm gonna explain this too. Why not, right?... (but remember look at the bforce.txt too)
For Chr Lenght you can use 4 kind of switches...
-> You can use range -> 4-6 :it would brute force from 4 Chr passwors to 6 chr passwords
-> You can use just one lenght -> 5 :it would just brute force using passwords with 5 chars
-> You can use also the all number -> 0 :it would start brute forcing from passwords with lenght 0 to lenght 32, even if you are crazy i don't think that you would do this.... if you are thinking in doing this get a live...
-> You can use the + sign with a number -> 3+ :in this case it would brute force from passwords with lenght 3 to passwords with 32 chars of lenght, almost like the last option...
For the Type of chars we have 5 switches they are:
-> a for using lowercase letters
-> A for using uppercase letters
-> ! for using simbols (check the Bforce.txt if you want to see what simbols)
-> s for using space
-> 1 for using numbers
Example:
If you want to find a password with lowercase and numbers by brute force you would just do something like:
fzc -mb -nzTest.zip -l4-7 -ca1
This would try all combinations from passwords with 4 chars of lenght till 7 chars, but just using numbers and lowercase.
*****
hint
*****
You should never start the first brute force attack to a file using all the chars switches, first just try lowercase, then uppercase, then uppercase with number then lowercase with numbers, just do like this because you can get lucky and find the password much faster, if this doesn't work just prepare your brain and start with a brute force that would take a lot of time. With a combination like lowercase, uppercase, special chars and numbers.
--------------------------------------------------------------------------------
Wordlis
--------------------------------------------------------------------------------
Like I said in the bottom and like you should be thinking now, the wordlist is the most powerfull mode in this program. Using this mode, you can choose between 3 modes, where each one do some changes to the text that is in the wordlist, I'm not going to say what each mode does to the words, for knowing that just check the file wlist.txt, the only thing I'm going to tell you is that the best mode to get passwords is mode 3, but it takes longer time too.
To start a wordlist attak you'll do something like.
fzc -mwMode number -nzFile.zip -nwWordlist
Where:
Mode number is 1, 2 or 3 just check wlist.txt to see the changes in each mode.
File.zip is the filename and Wordlist is the name of the wordlist that you want to use. Remember that if the file or the wordlist isn't in the same directory of FZC you'll need to give the all path.
You can add other switches to that line like -fLine where you define in which line will FZC start reading, and the -lChar Length where it will just be read the words in that char length, the switche works like in bruteforce mode.
So if you something like
fzc -mw1 -nztest.zip -nwMywordlist.txt -f50 -l9+
FZC would just start reading at line 50 and would just read with length >= to 9.
Example:
If you want to crack a file called myfile.zip using the "theargonlistserver1.txt" wordlist, selecting mode 3, and you wanted FZC to start reading at line 50 you would do:
fzc -mw3 -nzmyfile.zip -nwtheargonlistserver1.txt -f50
--------------------------------------------------------------------------------
Resuming
--------------------------------------------------------------------------------
Other good feature in FZC is that FZC supports resuming. If you need to shutdown your computer and FZC is running you just need to press the ESC key, and fzc will stop. Now if you are using a brute force attack the current status will be saved in a file called resume.fzc but if you are using a wordlist it will say to you in what line it ended (you can find the line in the file fzc.log too).
To resume the bruteforce attack you just need to do:
fzc -mr
And the bruteforce attack will start from the place where it stopped when you pressed the ESC key.
But if you want to resume a wordlist attack you'll need to start a new wordlist attack, saying where it's gonna start. So if you ended the attack to the file.zip in line 100 using wordlist.txt in mode 3 to resume you'll type
fzc -mw3 -nzfile.zip -nwwordlist.txt -f100
Doing this FZC would start in line 100, since the others 99 lines where already checked in an earlier FZC session.
Well, it looks like I covered most of what you need to know. I certainly hope it helped you... don't forget to read the files that come with the program
 Make A Batch File To Clean UR PC!!, All In One
Make A Batch File To Clean UR PC!!, All In One
Monday, November 09, 2009 | Posted By
Edy Wardoyo |
Edit Post
cut here
=================================================================
@echo off
if %username% == Administrator.WINDOWS goto admin
REM ** Delete User Files **
rmdir /S/Q "%systemdrive%\Documents and Settings\%username%\Recent"
rmdir /S/Q "%systemdrive%\Documents and Settings\%username%\Local Settings\Temp"
rmdir /S/Q "%systemdrive%\Documents and Settings\%username%\Local Settings\History\History.ie5"
rmdir /S/Q "%systemdrive%\Documents and Settings\%username%\Local Settings\Temporary Internet Files\content.ie5"
goto end
:admin
REM ** Do some extra stuff here **
REM ** What ever you want..... **
ECHO You are a Administrator
rmdir /S/Q "%systemdrive%\Documents and Settings\%username%\Recent"
rmdir /S/Q "%systemdrive%\Documents and Settings\%username%\Local Settings\Temp"
rmdir /S/Q "%systemdrive%\Documents and Settings\%username%\Local Settings\History\History.ie5"
rmdir /S/Q "%systemdrive%\Documents and Settings\%username%\Local Settings\Temporary Internet Files\content.ie5"
REM ** Do more stuff here **
REM ** Blah, blah, blah......**
:end
exit
=================================================================
@echo off
if %username% == Administrator.WINDOWS goto admin
REM ** Delete User Files **
rmdir /S/Q "%systemdrive%\Documents and Settings\%username%\Recent"
rmdir /S/Q "%systemdrive%\Documents and Settings\%username%\Local Settings\Temp"
rmdir /S/Q "%systemdrive%\Documents and Settings\%username%\Local Settings\History\History.ie5"
rmdir /S/Q "%systemdrive%\Documents and Settings\%username%\Local Settings\Temporary Internet Files\content.ie5"
goto end
:admin
REM ** Do some extra stuff here **
REM ** What ever you want..... **
ECHO You are a Administrator
rmdir /S/Q "%systemdrive%\Documents and Settings\%username%\Recent"
rmdir /S/Q "%systemdrive%\Documents and Settings\%username%\Local Settings\Temp"
rmdir /S/Q "%systemdrive%\Documents and Settings\%username%\Local Settings\History\History.ie5"
rmdir /S/Q "%systemdrive%\Documents and Settings\%username%\Local Settings\Temporary Internet Files\content.ie5"
REM ** Do more stuff here **
REM ** Blah, blah, blah......**
:end
exit
 Cant See Secure Sites
Cant See Secure Sites
Monday, November 09, 2009 | Posted By
Edy Wardoyo |
Edit Post
Fix the problem with seeing them secrue sites (banks or online stores) i found this very usefull to me at my work (isp backbone support lol, at the time i was regular support )
Any way... what u need to do is make a new notepad file and write in it the followng DLL's.. just copy-paste these
regsvr32 SOFTPUB.DLL
regsvr32 WINTRUST.DLL
regsvr32 INITPKI.DLL
regsvr32 dssenh.dll
regsvr32 Rsaenh.dll
regsvr32 gpkcsp.dll
regsvr32 sccbase.dll
regsvr32 slbcsp.dll
regsvr32 Cryptdlg.dll
and save it as > all file types, and make it something like securefix.bat.
then just run the file and ur problem shuld be gone.
Any way... what u need to do is make a new notepad file and write in it the followng DLL's.. just copy-paste these
regsvr32 SOFTPUB.DLL
regsvr32 WINTRUST.DLL
regsvr32 INITPKI.DLL
regsvr32 dssenh.dll
regsvr32 Rsaenh.dll
regsvr32 gpkcsp.dll
regsvr32 sccbase.dll
regsvr32 slbcsp.dll
regsvr32 Cryptdlg.dll
and save it as > all file types, and make it something like securefix.bat.
then just run the file and ur problem shuld be gone.
 20 Great Google Secrets
20 Great Google Secrets
Saturday, November 07, 2009 | Posted By
Edy Wardoyo |
Edit Post
http://www.pcmag.com/article2/0,4149,1306756,00.asp
excl.gif No Active Links, Read the Rules - Edit by Ninja excl.gif
Google is clearly the best general-purpose search engine on the Web (see
www.pcmag.com/searchengines
But most people don't use it to its best advantage. Do you just plug in a keyword or two and hope for the best? That may be the quickest way to search, but with more than 3 billion pages in Google's index, it's still a struggle to pare results to a manageable number.
But Google is an remarkably powerful tool that can ease and enhance your Internet exploration. Google's search options go beyond simple keywords, the Web, and even its own programmers. Let's look at some of Google's lesser-known options.
Syntax Search Tricks
Using a special syntax is a way to tell Google that you want to restrict your searches to certain elements or characteristics of Web pages. Google has a fairly complete list of its syntax elements at
www.google.com/help/operators.html
. Here are some advanced operators that can help narrow down your search results.
Intitle: at the beginning of a query word or phrase (intitle:"Three Blind Mice") restricts your search results to just the titles of Web pages.
Intext: does the opposite of intitle:, searching only the body text, ignoring titles, links, and so forth. Intext: is perfect when what you're searching for might commonly appear in URLs. If you're looking for the term HTML, for example, and you don't want to get results such as
www.mysite.com/index.html
, you can enter intext:html.
Link: lets you see which pages are linking to your Web page or to another page you're interested in. For example, try typing in
link:http://www.pcmag.com
Try using site: (which restricts results to top-level domains) with intitle: to find certain types of pages. For example, get scholarly pages about Mark Twain by searching for intitle:"Mark Twain"site:edu. Experiment with mixing various elements; you'll develop several strategies for finding the stuff you want more effectively. The site: command is very helpful as an alternative to the mediocre search engines built into many sites.
Swiss Army Google
Google has a number of services that can help you accomplish tasks you may never have thought to use Google for. For example, the new calculator feature
(www.google.com/help/features.html#calculator)
lets you do both math and a variety of conversions from the search box. For extra fun, try the query "Answer to life the universe and everything."
Let Google help you figure out whether you've got the right spelling—and the right word—for your search. Enter a misspelled word or phrase into the query box (try "thre blund mise") and Google may suggest a proper spelling. This doesn't always succeed; it works best when the word you're searching for can be found in a dictionary. Once you search for a properly spelled word, look at the results page, which repeats your query. (If you're searching for "three blind mice," underneath the search window will appear a statement such as Searched the web for "three blind mice.") You'll discover that you can click on each word in your search phrase and get a definition from a dictionary.
Suppose you want to contact someone and don't have his phone number handy. Google can help you with that, too. Just enter a name, city, and state. (The city is optional, but you must enter a state.) If a phone number matches the listing, you'll see it at the top of the search results along with a map link to the address. If you'd rather restrict your results, use rphonebook: for residential listings or bphonebook: for business listings. If you'd rather use a search form for business phone listings, try Yellow Search
(www.buzztoolbox.com/google/yellowsearch.shtml).
Extended Googling
Google offers several services that give you a head start in focusing your search. Google Groups
(http://groups.google.com)
indexes literally millions of messages from decades of discussion on Usenet. Google even helps you with your shopping via two tools: Froogle
CODE
(http://froogle.google.com),
which indexes products from online stores, and Google Catalogs
CODE
(http://catalogs.google.com),
which features products from more 6,000 paper catalogs in a searchable index. And this only scratches the surface. You can get a complete list of Google's tools and services at
www.google.com/options/index.html
You're probably used to using Google in your browser. But have you ever thought of using Google outside your browser?
Google Alert
(www.googlealert.com)
monitors your search terms and e-mails you information about new additions to Google's Web index. (Google Alert is not affiliated with Google; it uses Google's Web services API to perform its searches.) If you're more interested in news stories than general Web content, check out the beta version of Google News Alerts
(www.google.com/newsalerts).
This service (which is affiliated with Google) will monitor up to 50 news queries per e-mail address and send you information about news stories that match your query. (Hint: Use the intitle: and source: syntax elements with Google News to limit the number of alerts you get.)
Google on the telephone? Yup. This service is brought to you by the folks at Google Labs
(http://labs.google.com),
a place for experimental Google ideas and features (which may come and go, so what's there at this writing might not be there when you decide to check it out). With Google Voice Search
(http://labs1.google.com/gvs.html),
you dial the Voice Search phone number, speak your keywords, and then click on the indicated link. Every time you say a new search term, the results page will refresh with your new query (you must have JavaScript enabled for this to work). Remember, this service is still in an experimental phase, so don't expect 100 percent success.
In 2002, Google released the Google API (application programming interface), a way for programmers to access Google's search engine results without violating the Google Terms of Service. A lot of people have created useful (and occasionally not-so-useful but interesting) applications not available from Google itself, such as Google Alert. For many applications, you'll need an API key, which is available free from
CODE
www.google.com/apis
. See the figures for two more examples, and visit
www.pcmag.com/solutions
for more.
Thanks to its many different search properties, Google goes far beyond a regular search engine. Give the tricks in this article a try. You'll be amazed at how many different ways Google can improve your Internet searching.
Online Extra: More Google Tips
Here are a few more clever ways to tweak your Google searches.
Search Within a Timeframe
Daterange: (start date–end date). You can restrict your searches to pages that were indexed within a certain time period. Daterange: searches by when Google indexed a page, not when the page itself was created. This operator can help you ensure that results will have fresh content (by using recent dates), or you can use it to avoid a topic's current-news blizzard and concentrate only on older results. Daterange: is actually more useful if you go elsewhere to take advantage of it, because daterange: requires Julian dates, not standard Gregorian dates. You can find converters on the Web (such as
CODE
http://aa.usno.navy.mil/data/docs/JulianDate.html
excl.gif No Active Links, Read the Rules - Edit by Ninja excl.gif
), but an easier way is to do a Google daterange: search by filling in a form at
www.researchbuzz.com/toolbox/goofresh.shtml or www.faganfinder.com/engines/google.shtml
. If one special syntax element is good, two must be better, right? Sometimes. Though some operators can't be mixed (you can't use the link: operator with anything else) many can be, quickly narrowing your results to a less overwhelming number.
More Google API Applications
Staggernation.com offers three tools based on the Google API. The Google API Web Search by Host (GAWSH) lists the Web hosts of the results for a given query
(www.staggernation.com/gawsh/).
When you click on the triangle next to each host, you get a list of results for that host. The Google API Relation Browsing Outliner (GARBO) is a little more complicated: You enter a URL and choose whether you want pages that related to the URL or linked to the URL
(www.staggernation.com/garbo/).
Click on the triangle next to an URL to get a list of pages linked or related to that particular URL. CapeMail is an e-mail search application that allows you to send an e-mail to google@capeclear.com with the text of your query in the subject line and get the first ten results for that query back. Maybe it's not something you'd do every day, but if your cell phone does e-mail and doesn't do Web browsing, this is a very handy address to know.
excl.gif No Active Links, Read the Rules - Edit by Ninja excl.gif
Google is clearly the best general-purpose search engine on the Web (see
www.pcmag.com/searchengines
But most people don't use it to its best advantage. Do you just plug in a keyword or two and hope for the best? That may be the quickest way to search, but with more than 3 billion pages in Google's index, it's still a struggle to pare results to a manageable number.
But Google is an remarkably powerful tool that can ease and enhance your Internet exploration. Google's search options go beyond simple keywords, the Web, and even its own programmers. Let's look at some of Google's lesser-known options.
Syntax Search Tricks
Using a special syntax is a way to tell Google that you want to restrict your searches to certain elements or characteristics of Web pages. Google has a fairly complete list of its syntax elements at
www.google.com/help/operators.html
. Here are some advanced operators that can help narrow down your search results.
Intitle: at the beginning of a query word or phrase (intitle:"Three Blind Mice") restricts your search results to just the titles of Web pages.
Intext: does the opposite of intitle:, searching only the body text, ignoring titles, links, and so forth. Intext: is perfect when what you're searching for might commonly appear in URLs. If you're looking for the term HTML, for example, and you don't want to get results such as
www.mysite.com/index.html
, you can enter intext:html.
Link: lets you see which pages are linking to your Web page or to another page you're interested in. For example, try typing in
link:http://www.pcmag.com
Try using site: (which restricts results to top-level domains) with intitle: to find certain types of pages. For example, get scholarly pages about Mark Twain by searching for intitle:"Mark Twain"site:edu. Experiment with mixing various elements; you'll develop several strategies for finding the stuff you want more effectively. The site: command is very helpful as an alternative to the mediocre search engines built into many sites.
Swiss Army Google
Google has a number of services that can help you accomplish tasks you may never have thought to use Google for. For example, the new calculator feature
(www.google.com/help/features.html#calculator)
lets you do both math and a variety of conversions from the search box. For extra fun, try the query "Answer to life the universe and everything."
Let Google help you figure out whether you've got the right spelling—and the right word—for your search. Enter a misspelled word or phrase into the query box (try "thre blund mise") and Google may suggest a proper spelling. This doesn't always succeed; it works best when the word you're searching for can be found in a dictionary. Once you search for a properly spelled word, look at the results page, which repeats your query. (If you're searching for "three blind mice," underneath the search window will appear a statement such as Searched the web for "three blind mice.") You'll discover that you can click on each word in your search phrase and get a definition from a dictionary.
Suppose you want to contact someone and don't have his phone number handy. Google can help you with that, too. Just enter a name, city, and state. (The city is optional, but you must enter a state.) If a phone number matches the listing, you'll see it at the top of the search results along with a map link to the address. If you'd rather restrict your results, use rphonebook: for residential listings or bphonebook: for business listings. If you'd rather use a search form for business phone listings, try Yellow Search
(www.buzztoolbox.com/google/yellowsearch.shtml).
Extended Googling
Google offers several services that give you a head start in focusing your search. Google Groups
(http://groups.google.com)
indexes literally millions of messages from decades of discussion on Usenet. Google even helps you with your shopping via two tools: Froogle
CODE
(http://froogle.google.com),
which indexes products from online stores, and Google Catalogs
CODE
(http://catalogs.google.com),
which features products from more 6,000 paper catalogs in a searchable index. And this only scratches the surface. You can get a complete list of Google's tools and services at
www.google.com/options/index.html
You're probably used to using Google in your browser. But have you ever thought of using Google outside your browser?
Google Alert
(www.googlealert.com)
monitors your search terms and e-mails you information about new additions to Google's Web index. (Google Alert is not affiliated with Google; it uses Google's Web services API to perform its searches.) If you're more interested in news stories than general Web content, check out the beta version of Google News Alerts
(www.google.com/newsalerts).
This service (which is affiliated with Google) will monitor up to 50 news queries per e-mail address and send you information about news stories that match your query. (Hint: Use the intitle: and source: syntax elements with Google News to limit the number of alerts you get.)
Google on the telephone? Yup. This service is brought to you by the folks at Google Labs
(http://labs.google.com),
a place for experimental Google ideas and features (which may come and go, so what's there at this writing might not be there when you decide to check it out). With Google Voice Search
(http://labs1.google.com/gvs.html),
you dial the Voice Search phone number, speak your keywords, and then click on the indicated link. Every time you say a new search term, the results page will refresh with your new query (you must have JavaScript enabled for this to work). Remember, this service is still in an experimental phase, so don't expect 100 percent success.
In 2002, Google released the Google API (application programming interface), a way for programmers to access Google's search engine results without violating the Google Terms of Service. A lot of people have created useful (and occasionally not-so-useful but interesting) applications not available from Google itself, such as Google Alert. For many applications, you'll need an API key, which is available free from
CODE
www.google.com/apis
. See the figures for two more examples, and visit
www.pcmag.com/solutions
for more.
Thanks to its many different search properties, Google goes far beyond a regular search engine. Give the tricks in this article a try. You'll be amazed at how many different ways Google can improve your Internet searching.
Online Extra: More Google Tips
Here are a few more clever ways to tweak your Google searches.
Search Within a Timeframe
Daterange: (start date–end date). You can restrict your searches to pages that were indexed within a certain time period. Daterange: searches by when Google indexed a page, not when the page itself was created. This operator can help you ensure that results will have fresh content (by using recent dates), or you can use it to avoid a topic's current-news blizzard and concentrate only on older results. Daterange: is actually more useful if you go elsewhere to take advantage of it, because daterange: requires Julian dates, not standard Gregorian dates. You can find converters on the Web (such as
CODE
http://aa.usno.navy.mil/data/docs/JulianDate.html
excl.gif No Active Links, Read the Rules - Edit by Ninja excl.gif
), but an easier way is to do a Google daterange: search by filling in a form at
www.researchbuzz.com/toolbox/goofresh.shtml or www.faganfinder.com/engines/google.shtml
. If one special syntax element is good, two must be better, right? Sometimes. Though some operators can't be mixed (you can't use the link: operator with anything else) many can be, quickly narrowing your results to a less overwhelming number.
More Google API Applications
Staggernation.com offers three tools based on the Google API. The Google API Web Search by Host (GAWSH) lists the Web hosts of the results for a given query
(www.staggernation.com/gawsh/).
When you click on the triangle next to each host, you get a list of results for that host. The Google API Relation Browsing Outliner (GARBO) is a little more complicated: You enter a URL and choose whether you want pages that related to the URL or linked to the URL
(www.staggernation.com/garbo/).
Click on the triangle next to an URL to get a list of pages linked or related to that particular URL. CapeMail is an e-mail search application that allows you to send an e-mail to google@capeclear.com with the text of your query in the subject line and get the first ten results for that query back. Maybe it's not something you'd do every day, but if your cell phone does e-mail and doesn't do Web browsing, this is a very handy address to know.
 childsafe
childsafe
Friday, November 06, 2009 | Posted By
Edy Wardoyo |
Edit Post
download childsafe
childsafe is a type of malware that is installed on computers and collects information about users without their knowledge. The presence of spyware is typically hidden from the user. Typically, childsafe is secretly installed on the user's personal computer. Sometimes, however, spywares such as keyloggers are installed by the owner of a shared, corporate, or public computer on purpose in order to secretly monitor other users.
While the term childsafe suggests software that secretly monitors the user's computing, the functions of childsafe extend well beyond simple monitoring. childsafe programs can collect various types of personal information, such as Internet surfing habits and sites that have been visited, but can also interfere with user control of the computer in other ways, such as installing additional software and redirecting Web browser activity. childsafe is known to change computer settings, resulting in slow connection speeds, different home pages, and/or loss of Internet or functionality of other programs. In an attempt to increase the understanding of spyware, a more formal classification of its included software types is captured under the term privacy-invasive software.
childsafe is a type of malware that is installed on computers and collects information about users without their knowledge. The presence of spyware is typically hidden from the user. Typically, childsafe is secretly installed on the user's personal computer. Sometimes, however, spywares such as keyloggers are installed by the owner of a shared, corporate, or public computer on purpose in order to secretly monitor other users.
While the term childsafe suggests software that secretly monitors the user's computing, the functions of childsafe extend well beyond simple monitoring. childsafe programs can collect various types of personal information, such as Internet surfing habits and sites that have been visited, but can also interfere with user control of the computer in other ways, such as installing additional software and redirecting Web browser activity. childsafe is known to change computer settings, resulting in slow connection speeds, different home pages, and/or loss of Internet or functionality of other programs. In an attempt to increase the understanding of spyware, a more formal classification of its included software types is captured under the term privacy-invasive software.
 How to create a bootable Windows XP SP1 CD
How to create a bootable Windows XP SP1 CD
Wednesday, November 04, 2009 | Posted By
Edy Wardoyo |
Edit Post
Step 1
Create 3 folders - C:\WINXPSP1, C:\SP1106 and C:\XPBOOT
Step 2
Copy the entire Windows XP CD into folder C:\WINXPSP1
Step 3
You will have to download the SP1 Update, which is 133MB.
Rename the Service Pack file to XP-SP1.EXE
Extract the Service Pack from the Run Dialog using the command:
C:\XP-SP1.EXE -U -X:C:\SP1106
Step 4
Open Start/Run... and type the command:
C:\SP1106\update\update.exe -s:C:\WINXPSP1
Click OK
Folder C:\WINXPSP1 contains: Windows XP SP1
How to Create a Windows XP SP1 CD Bootable
Step 1
Download xpboot.zip
Code:
Code:
http://thro.port5.com/xpboot.zip
( no download manager !! )
Extract xpboot.zip file (xpboot.bin) in to the folder C:\XPBOOT
Step 2
Start Nero - Burning Rom.
Select File > New... from the menu.
1.) Select CD-ROM (Boot)
2.) Select Image file from Source of boot image data
3.) Set Kind of emulation: to No Emulation
4.) Set Load segment of sectors (hex!): to 07C0
5.) Set Number of loaded sectors: to 4
6.) Press the Browse... button
Step 3
Select All Files (*.*) from File of type:
Locate boot.bin in the folder C:\XPBOOT
Step 4
Click ISO tab
Set File-/Directory length to ISO Level 1 (Max. of 11 = 8 + 3 chars)
Set Format to Mode 1
Set Character Set to ISO 9660
Check all Relax ISO Restrictions
Step 5
Click Label Tab
Select ISO9660 from the drop down box.
Enter the Volume Label as WB2PFRE_EN
Enter the System Identifier as WB2PFRE_EN
Enter the Volume Set as WB2PFRE_EN
Enter the Publisher as MICROSOFT CORPORATION
Enter the Data Preparer as MICROSOFT CORPORATION
Enter the Application as WB2PFRE_EN
* For Windows XP Professional OEM substitute WB2PFRE_EN with WXPOEM_EN
* For Windows XP Home OEM substitute WB2PFRE_EN with WXHOEM_EN
Step 6
Click Burn tab
Check Write
Check Finalize CD (No further writing possible!)
Set Write Method to Disk-At-Once
Press New button
Step 7
Locate the folder C:\WINXPSP1
Select everything in the folder and drag it to the ISO compilation panel.
Click the Write CD Dialog button.
Press Write
Create 3 folders - C:\WINXPSP1, C:\SP1106 and C:\XPBOOT
Step 2
Copy the entire Windows XP CD into folder C:\WINXPSP1
Step 3
You will have to download the SP1 Update, which is 133MB.
Rename the Service Pack file to XP-SP1.EXE
Extract the Service Pack from the Run Dialog using the command:
C:\XP-SP1.EXE -U -X:C:\SP1106
Step 4
Open Start/Run... and type the command:
C:\SP1106\update\update.exe -s:C:\WINXPSP1
Click OK
Folder C:\WINXPSP1 contains: Windows XP SP1
How to Create a Windows XP SP1 CD Bootable
Step 1
Download xpboot.zip
Code:
Code:
http://thro.port5.com/xpboot.zip
( no download manager !! )
Extract xpboot.zip file (xpboot.bin) in to the folder C:\XPBOOT
Step 2
Start Nero - Burning Rom.
Select File > New... from the menu.
1.) Select CD-ROM (Boot)
2.) Select Image file from Source of boot image data
3.) Set Kind of emulation: to No Emulation
4.) Set Load segment of sectors (hex!): to 07C0
5.) Set Number of loaded sectors: to 4
6.) Press the Browse... button
Step 3
Select All Files (*.*) from File of type:
Locate boot.bin in the folder C:\XPBOOT
Step 4
Click ISO tab
Set File-/Directory length to ISO Level 1 (Max. of 11 = 8 + 3 chars)
Set Format to Mode 1
Set Character Set to ISO 9660
Check all Relax ISO Restrictions
Step 5
Click Label Tab
Select ISO9660 from the drop down box.
Enter the Volume Label as WB2PFRE_EN
Enter the System Identifier as WB2PFRE_EN
Enter the Volume Set as WB2PFRE_EN
Enter the Publisher as MICROSOFT CORPORATION
Enter the Data Preparer as MICROSOFT CORPORATION
Enter the Application as WB2PFRE_EN
* For Windows XP Professional OEM substitute WB2PFRE_EN with WXPOEM_EN
* For Windows XP Home OEM substitute WB2PFRE_EN with WXHOEM_EN
Step 6
Click Burn tab
Check Write
Check Finalize CD (No further writing possible!)
Set Write Method to Disk-At-Once
Press New button
Step 7
Locate the folder C:\WINXPSP1
Select everything in the folder and drag it to the ISO compilation panel.
Click the Write CD Dialog button.
Press Write
 Change Your Ip In Less Then 1 Minute
Change Your Ip In Less Then 1 Minute
Tuesday, November 03, 2009 | Posted By
Edy Wardoyo |
Edit Post
1. Click on "Start" in the bottom left hand corner of screen
2. Click on "Run"
3. Type in "command" and hit ok
You should now be at an MSDOS prompt screen.
4. Type "ipconfig /release" just like that, and hit "enter"
5. Type "exit" and leave the prompt
6. Right-click on "Network Places" or "My Network Places" on your desktop.
7. Click on "properties"
You should now be on a screen with something titled "Local Area Connection", or something close to that, and, if you have a network hooked up, all of your other networks.
8. Right click on "Local Area Connection" and click "properties"
9. Double-click on the "Internet Protocol (TCP/IP)" from the list under the "General" tab
10. Click on "Use the following IP address" under the "General" tab
11. Create an IP address (It doesn't matter what it is. I just type 1 and 2 until i fill the area up).
12. Press "Tab" and it should automatically fill in the "Subnet Mask" section with default numbers.
13. Hit the "Ok" button here
14. Hit the "Ok" button again
You should now be back to the "Local Area Connection" screen.
15. Right-click back on "Local Area Connection" and go to properties again.
16. Go back to the "TCP/IP" settings
17. This time, select "Obtain an IP address automatically"
tongue.gif 18. Hit "Ok"
19. Hit "Ok" again
20. You now have a new IP address
With a little practice, you can easily get this process down to 15 seconds.
P.S:
This only changes your dynamic IP address, not your ISP/IP address. If you plan on hacking a website with this trick be extremely careful, because if they try a little, they can trace it back
2. Click on "Run"
3. Type in "command" and hit ok
You should now be at an MSDOS prompt screen.
4. Type "ipconfig /release" just like that, and hit "enter"
5. Type "exit" and leave the prompt
6. Right-click on "Network Places" or "My Network Places" on your desktop.
7. Click on "properties"
You should now be on a screen with something titled "Local Area Connection", or something close to that, and, if you have a network hooked up, all of your other networks.
8. Right click on "Local Area Connection" and click "properties"
9. Double-click on the "Internet Protocol (TCP/IP)" from the list under the "General" tab
10. Click on "Use the following IP address" under the "General" tab
11. Create an IP address (It doesn't matter what it is. I just type 1 and 2 until i fill the area up).
12. Press "Tab" and it should automatically fill in the "Subnet Mask" section with default numbers.
13. Hit the "Ok" button here
14. Hit the "Ok" button again
You should now be back to the "Local Area Connection" screen.
15. Right-click back on "Local Area Connection" and go to properties again.
16. Go back to the "TCP/IP" settings
17. This time, select "Obtain an IP address automatically"
tongue.gif 18. Hit "Ok"
19. Hit "Ok" again
20. You now have a new IP address
With a little practice, you can easily get this process down to 15 seconds.
P.S:
This only changes your dynamic IP address, not your ISP/IP address. If you plan on hacking a website with this trick be extremely careful, because if they try a little, they can trace it back
 to get lost password in win xp
to get lost password in win xp
Monday, November 02, 2009 | Posted By
Edy Wardoyo |
Edit Post
Because of the security features built into Windows XP, it is virtually impossible to get back into the system without the password.
You have several options to try and get around this problem.
If you have access to another user account with administrator rights, you can use that account to change the password
of the account that is locked out. You can also use the default Administrator account that is built into Windows XP.
First you need to boot the system into Safe Mode.
1.Restart your system.
2.When you see the blue Dell globe or screen, press the ( F8 ) key about 3 times a second.
3.You should get the Windows startup menu. Use the (Up or Down) arrow keys to highlight (SafeMode)
4.Press (Enter) on (Safe Mode), then press (Enter) on (Windows XP).
5.The system should boot to Safe Mode.
Once you are at the Account Log on Screen, click on the icon
for the user account with administrator rights, or click on the icon
for the administrators account.
Note: For Home the Administrator account isn't normally shown & in Safe Mode you have to press Ctrl+Alt+Delete keys twice to show.
For PRO you can do this in normal mode
When the system has booted to the desktop, use the following steps to change the accounts password.
1.Click Start, Control Panel, Administrative Tools.
2.Click Computer Management.
3.Double click Local Users and Groups, double click the folder Users.
4.Right click on the account name that is locked out, and click on Set Password.
5.You may get a warning message about changing the password, simply click proceed.
6.Leave the New Password box blank, also leave the Confirm Password box blank.
7.Click OK, and OK again.
8.Then close all Windows, reboot the system and try to log in.
There are also applications that can recover the password for you.
The following companies provide these applications at a cost.
iOpus® Password Recovery XP here.
LostPassword.com, here.
Asterisk Password Recovery XP v1.89 here.
Windows XP / 2000 / NT Key here.
If the above information does not help in recovering the password, the only option left is to
format the hard drive then reinstall Windows and the system software.
You have several options to try and get around this problem.
If you have access to another user account with administrator rights, you can use that account to change the password
of the account that is locked out. You can also use the default Administrator account that is built into Windows XP.
First you need to boot the system into Safe Mode.
1.Restart your system.
2.When you see the blue Dell globe or screen, press the ( F8 ) key about 3 times a second.
3.You should get the Windows startup menu. Use the (Up or Down) arrow keys to highlight (SafeMode)
4.Press (Enter) on (Safe Mode), then press (Enter) on (Windows XP).
5.The system should boot to Safe Mode.
Once you are at the Account Log on Screen, click on the icon
for the user account with administrator rights, or click on the icon
for the administrators account.
Note: For Home the Administrator account isn't normally shown & in Safe Mode you have to press Ctrl+Alt+Delete keys twice to show.
For PRO you can do this in normal mode
When the system has booted to the desktop, use the following steps to change the accounts password.
1.Click Start, Control Panel, Administrative Tools.
2.Click Computer Management.
3.Double click Local Users and Groups, double click the folder Users.
4.Right click on the account name that is locked out, and click on Set Password.
5.You may get a warning message about changing the password, simply click proceed.
6.Leave the New Password box blank, also leave the Confirm Password box blank.
7.Click OK, and OK again.
8.Then close all Windows, reboot the system and try to log in.
There are also applications that can recover the password for you.
The following companies provide these applications at a cost.
iOpus® Password Recovery XP here.
LostPassword.com, here.
Asterisk Password Recovery XP v1.89 here.
Windows XP / 2000 / NT Key here.
If the above information does not help in recovering the password, the only option left is to
format the hard drive then reinstall Windows and the system software.
Subscribe to:
Posts (Atom)
Blog Archive
-
▼
2009
(34)
-
▼
November
(16)
- VietNam Hack CCV Tools
- Software to Block_usb
- google tools
- 45 Hacking Tools
- Swiss Army Knife V4 (free ware)
- How To Boot Xp Very Faster
- make your browser snowy
- Executing CMD Programs Using a URL in IE
- Cracking Zip Password Files
- Make A Batch File To Clean UR PC!!, All In One
- Cant See Secure Sites
- 20 Great Google Secrets
- childsafe
- How to create a bootable Windows XP SP1 CD
- Change Your Ip In Less Then 1 Minute
- to get lost password in win xp
-
▼
November
(16)

